지난해 북한의 암호화폐 해킹 공격이 전년도에 비해 2배 이상 급증한 것으로 나타났습니다. 북한 IT 노동자들이 위장취업을 통해 암호화폐 기업 네트워크에 침투하는 사례가 증가한 것과 관련이 있는 것으로 분석됐습니다. 조상진 기자가 보도합니다.
미국의 암호화폐 분석기업인 체이널리시스는 27일 발표한 ‘2025암호화폐 범죄 보고서’에서 “지난해 북한 해커들이 암호화폐 플랫폼에서 그 어느 때보다도 더 많이 훔쳤다”고 지적했습니다.
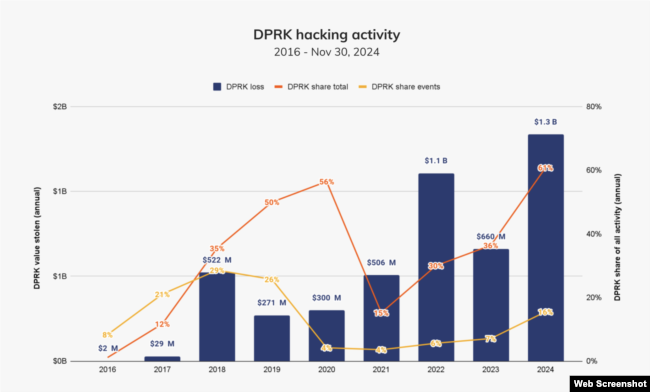
[보고서] “In 2024, North Korean hackers stole more from crypto platforms than ever before. In 2023, North Korea-affiliated hackers stole approximately $660.50 million across 20 incidents; in 2024, this number increased to $1.34 billion stolen across 47 incidents — a 102.88% increase in value stolen. These figures represent 61% of the total amount stolen for the year, and 20% of total incidents.”
체이널리시스는 보고서에서 지난 2023년 총 20건의 사건을 통해 약 6억 6050만 달러를 탈취했던 북한 연계 해커들이 지난해에는 총 47건의 사건에서 13억 4천만 달러를 훔쳐, 탈취 금액 기준으로 102.88%가 증가했다고 밝혔습니다. 사건 발생 건수 역시 전년 대비 2배 이상 증가했습니다.
<“북한, 해킹 주기 짧아지고 성공률 높아져”>
그러면서 지난해 탈취된 전체 암호화폐 금액에서 북한이 차지하는 비중이 61%이며, 전체 사건 수에서는 북한이 20%를 차지한다고 지적했습니다. 보고서는 또 북한의 암호화폐 해킹 공격 사이 간격을 분석한 결과 해킹이 발생하는 주기가 점점 더 짧아지고 있는 것으로 나타났으며, 성공하는 빈도도 증가하고 있다고 평가했습니다.
특히 지난해에는 5천만~1억 달러 이상의 대규모 공격이 전년도에 비해 크게 증가했다면서, 이는 북한이 대형 해킹을 더욱 효과적이고 신속하게 수행하고 있음을 시사하며, 과거 2년간 주로 5천만 달러 이하의 해킹 공격을 통해 수익을 올리던 경향과 뚜렷한 대비를 이룬다고 지적했습니다.
보고서는 북한의 암호화폐 분야 해킹 공격 횟수와 탈취 금액이 크게 늘어난 것은 “암호화폐 관련 기업에 침투해 그들의 네트워크, 운영, 무결성을 훼손하는 북한의 IT 노동자들과 관련이 있다”고 진단했습니다.
[보고서] “Some of these events appear to be linked to North Korean IT workers, who have been increasingly infiltrating crypto and Web3 companies, and compromising their networks, operations, and integrity. These workers often use sophisticated Tactics, Techniques, and Procedures (TTPs), such as false identities, third-party hiring intermediaries, and manipulating remote work opportunities to gain access.”
<“북한 IT 인력, 암호화폐 해킹 증가 기여”>
북한 IT 인력들이 암호화폐 기업 내부 접근 권한을 확보하기 위해 가짜 신분, 제3자 채용 중개업체 활용, 원격 근무 기회 조작과 같은 정교한 전술 및 기법, 절차를 활용하고 있다는 것입니다. 그러면서 이러한 위험을 완화하기 위해 기업들은 신원 조회 및 신원 확인 등 채용시 적극적인 실사를 실시해야 하며, 필요한 경우 주요 자산 보호를 위한 강력한 개인 키 관리 정책을 유지해야 한다고 지적했습니다.
보고서는 또 지난해 6월 블라디미르 푸틴 러시아 대통령과 김정은 국무위원장이 평양에서 만나 정상회담을 갖고 상호 방위 조약을 체결한 이후 북한의 해킹 활동에 큰 변화가 있었던 점에도 주목했습니다. 지난해 7월 1일 기준으로 상반기와 하반기 북한 해커들의 암호화폐 탈취 활동을 비교한 결과, 정상회담 이후 북한의 해킹 활동이 약 54% 감소했다는 것입니다.
그러면서 북한의 해킹이 줄어든 것은 정권이 군사 및 정보 분야 모든 역량을 우크라이나 전쟁 지원으로 돌렸기 때문일 가능성이 있으며, 러시아와의 협력이 강화되면서 사이버 활동에도 전략적인 변화가 있었을 가능성이 있다고 분석했습니다.
이번 보고서 작성에 참여한 앤드류 피어먼 체이널리시스 국가안보정보 팀장은 28일 VOA에 “북한의 지원을 받는 사이버 해킹조직과 악의적 행위자들이 점점 더 정교해지고 있다”고 지적했습니다.
[피어먼 팀장] “As DPRK-backed cyber attackers and bad actors are becoming more sophisticated. Cryptocurrency businesses must take a proactive approach to threat prevention. Real-time monitoring and advanced predictive technologies for detecting emerging threats will become essential. Exchanges will also need to demonstrate to their regulators and users how they ensure that user funds are protected.”
그러면서 “암호화폐 기업들은 위협 예방을 위해 더욱 적극적으로 대처해야 한다”며, 실시간 모니터링과 새 위협을 감지하는 고급 예측 기술을 필수적으로 도입해야 한다고 강조했습니다. 아울러 암호화폐 거래소들도 규제 기관과 사용자에게 그들의 자금이 어떻게 보호되고 있는지 계속 입증해야 한다고 덧붙였습니다.
피어먼 팀장은 또 북한 해커들이 훔친 자금을 세탁하고 현금화하는 역량을 방해하는 것도 무엇보다 중요한 과제라면서, 당국과 사이버 보안 기업이 북한 등 악성 행위자들의 불법 활동을 실시간으로 추적하고 모니터링할 수 있는 블록체인 보안 기술을 더욱 적극적으로 활용해야 한다고 강조했습니다.